"대문"의 두 판 사이의 차이
Hunter0x01 (토론 | 기여) 잔글 |
Hunter0x01 (토론 | 기여) 잔글 |
||
| 73번째 줄: | 73번째 줄: | ||
== shell 예제 == | == shell 예제 == | ||
https://www.codegrepper.com/code-examples/shell/ | https://www.codegrepper.com/code-examples/shell/ | ||
| + | |||
| + | |||
| + | == 인터넷 익스플로러 호환성 모드 추가 == | ||
| + | 기존 인터넷 익스플로러 호환성 모드 추가해놓고 레지스트리 가서 export 받아 hex "," 없애고 reg add 로 추가 | ||
| + | |||
| + | <source lang="bash"> | ||
| + | set regkey="HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\BrowserEmulation\ClearableListData" | ||
| + | set regdata=411f00005308adba010000003000000001000000010000000c000000b2981b841013d2010100000009006b00720061002e0063006f002e006b007200 | ||
| + | reg add %regkey% /v UserFilter /t REG_BINARY /d %regdata% | ||
| + | </source> | ||
2022년 5월 11일 (수) 07:39 판
목차
RUST 프로그래밍
https://rinthel.github.io/rust-lang-book-ko/
https://github.com/PacktPublishing/Practical-System-Programming-for-Rust-Developers
CVE-2021-44228 Log4Shell (PoC)
https://github.com/search?q=CVE-2021-44228&ref=simplesearch
Quick
root@SMEV:/root> lsof -n -P -iTCP -sTCP:LISTEN
https://me2nuk.com/Python-requests-module-example/
https://hackcatml.tistory.com/19
oscp 서바이벌 가이드
https://github.com/wwong99/pentest-notes/blob/master/oscp_resources/OSCP-Survival-Guide.md
https://sda.pu.go.id/tkpsda/saddang/uploads/buletin/buletin_201606091844.pdf
https://emaragkos.gr/resources/
lena 리버싱 한글
https://github.com/re4lfl0w/lena_reversing
reversing
Reversing for everyone
https://0xinfection.github.io/reversing/
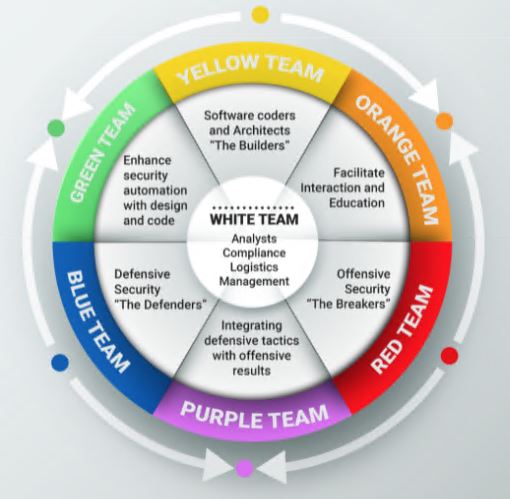
팀별 구분
기타
https://github.com/infosecn1nja
admin 템플릿
https://themewagon.com/theme-category/admin-dashboard/
reverse engineering
https://gist.github.com/ik5/0876fc87917fbf531b70c7fda7afdc3b
https://docs.google.com/spreadsheets/u/0/d/13wBzwmfAoEBPUgcYM4CgSoj--xLicPz777IQ6iSUlNk/htmlview#
300TB
https://drive.google.com/drive/folders/1oCMgJeBc55NuEasPcgwjx2FuPdQd8neu
pentester academy
https://mega.nz/folder/SDhkwaQD#R1ij2jAibi4Mqv8CxxkS0w
Offensive Security Mindmap
https://awesomeopensource.com/project/Zeyad-Azima/Offensive-Resources
pentester 2
https://hide01.ir/downloads/category/hide01/penetration-testing/pentester-academy-red/
테크트리
https://www.lazenca.net/display/TEC/02.TechNote
https://doongdangdoongdangdong.tistory.com/172
shell 예제
https://www.codegrepper.com/code-examples/shell/
인터넷 익스플로러 호환성 모드 추가
기존 인터넷 익스플로러 호환성 모드 추가해놓고 레지스트리 가서 export 받아 hex "," 없애고 reg add 로 추가
set regkey="HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\BrowserEmulation\ClearableListData"
set regdata=411f00005308adba010000003000000001000000010000000c000000b2981b841013d2010100000009006b00720061002e0063006f002e006b007200
reg add %regkey% /v UserFilter /t REG_BINARY /d %regdata%